OpenVPN is the recommended protocol for desktops including Windows, Mac OS X and Linux. Chameleon is great for VPN users being blocked in countries such as China, or if you are experiencing speed issues due to bandwidth throttling. IPSec SSL Performance Operates via a piece of software on the client, so it may take a while longer to negotiate connections. Operates via web browsers, making it slightly faster when it comes to negotiating a connection.
Control Broad access to the internal network or applications, which can lead to security concerns. More granular access control, but requires more management.
Comparison of VPN protocols
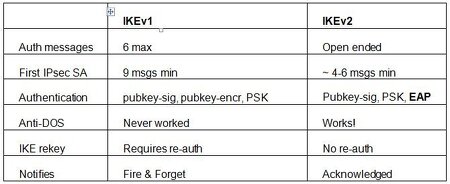
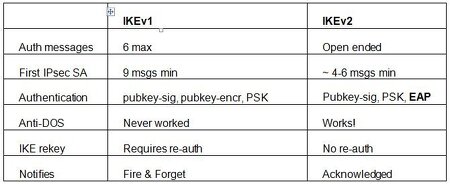
Data Authentication Internet Key Exchange (IKE) Key exchange algorithms like Elliptic Curve Cryptography (ECC) and RSA. Protect Against Attacks Since it provides remote access to the entire network, the attack surface is wide. Limited attack surface as it enables remote access to specific applications and systems.
A great alternative to OpenVPN.Has promise to be fast and efficient. Still in development.Faster and more secure alternative to PPTP and L2TP.Secure, stable, and mobile-oriented. Both TCP and UDP OpenVPN connections will offer excellent security and privacy when using your VPN service.
Access Server
OpenVPN is both an open-source VPN protocol and VPN software that enables people to run secured VPN connections. Most VPN providers offer this protocol because it’s very secure (it uses the OpenSSL library and 256-bit encryption) and it works across multiple platforms. OpenVPN is considered the best choice among VPN protocols, with only SoftEther being able to rival it. Requires third-party software.Strong Windows desktop support.Multiple device and platform support.Multiple desktop and mobile OS support.
Fast speeds, even on connections with high latency and across great distances. Most reliable and stable, even behind wireless routers, on non-reliable networks, and on Wi-Fi hotspots. Masks VPN traffic so it cannot be identified as a VPN connection (via deep packet inspection) and blocked.
OpenVPN can run over User Datagram Protocol (UDP) or Transmission Control Protocol (TCP) tunnel transports. This makes your web traffic indistinguishable from the traffic using standard HTTPS over SSL, and it is therefore extremely difficult to detect and block. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses. Another important difference is that IPsec does not explicitly specify encryption of connections, while SSL VPNs default to encryption of network traffic.
Is IPSec better than OpenVPN?
IPSec with IKEv2 should in theory be the faster than OpenVPN due to user-mode encryption in OpenVPN however it depends on many variables specific to the connection. In most cases it is faster than OpenVPN. IPSec is more complex than OpenVPN and can require additional configuration between devices behind NAT routers.
Personal VPN
IPsec, also known as Internet Protocol Security, defines the official architecture for securing IP network traffic. IPsec specifies ways in which IP hosts can encrypt and authenticate data being sent at the IP network layer. IPsec is used to create a secure tunnel between entities that are identified by their IP addresses. IPsec VPNs typically are used to connect a remote host with a network VPN server; the traffic sent over the public internet is encrypted between the VPN server and the remote host.
The choice between the two really depends on your own speed requirements and whether your connecting from your work or home network. Operating at the transport layer also means that an external attacker monitoring network traffic may be able to identify the application protocols being used by remote users. SSL VPNs can be implemented without the need to install client software on remote hosts because modern TLS-enabled browser clients can be used to create secured tunnels. Modern SSL VPNs actually use TLS to encrypt streams of network data being sent between processes. The TLS protocol enables encryption and authentication of connections between programs.
IPsec enables the communicating hosts to negotiate which cryptographic algorithms are to be used to encrypt or authenticate data. No discussion of VPNs would be complete without mentioning SSH, which can be used to enable secure tunnels between clients and servers. SSH implements its own encryption and authentication protocols to enable secure circuits between a client and server. It is sometimes used as a sort of ad hoc VPN, such as when remote users log in to their work system to access services and systems within the enterprise network. IPsec, also known as the Internet Protocol Security or IP Security protocol, defines the architecture for security services for IP network traffic.
- Fast speeds, even on connections with high latency and across great distances.
OpenVPN/SSL was until quite recently considered the best VPN combination for most users of consumer VPNs. OpenVPN, which uses the OpenSSL library for encryption and authentication, is reasonably fast, very secure, open source, and can traverse NAT firewalls. VPN encryption prevents third parties from reading your data as it passes through the internet.
These connections are usually defined by the IP addresses of the endpoints, as well as the port numbers of the programs running on those endpoints. TLS enables the communicating hosts to negotiate which cryptographic algorithms are to be used to encrypt or authenticate data. While some configurations permit the use of deprecated SSL versions, security best practices recommend using only the latest versions of TLS. SSTP and OpenVPN are pretty similar since they both use SSL 3.0, and both VPN protocols can use port 443.
VPN protocols that use IPSec encryption include L2TP, IKEv2, and SSTP. OpenVPN is the most popular protocol that uses SSL encryption, specifically the OpenSSL library. OpenVPN is one of the youngest, since it was released in 2001, and widely used open-source technology, i.e. everyone can freely use it and modify it as needed. It uses a custom security protocol that utilizes SSL/TLS for key exchange, creating secure point-to-point or site-to-site connections.
Does OpenVPN use IPSec?
IPsec (client) is already included in Windows and Android. Also, IPsec is easier to configure on the client side at least whereas OpenVPN requires either open source or proprietary app. So, both have pros and cons, thus should not be seen as better or worse but more like a tool to use to get a job done.
Security Supports replay protection, network-level authentication as well as data integrity and confidentiality. Uses SSL or TLS for encryption as well as public keys, private keys, and digital certificates for authentication. Ease of Use The implementation and configuration process is typically lengthy. Suitable for bypassing firewalls as it uses port 443 – the default port for secure HTTPS traffic.
Currently, it’s one of the most popular VPN protocols among VPN users. With encapsulation, the data packets that are at the core of Internet communication are wrapped inside another type of packet.
This is an authentication protocol that needs to be paired with a tunneling suite to make it suitable for VPN encryption purposes. IPsec is usually combined with L2TP to make L2TP/IPsec or with IKEv2 to make IKEv2/IPsec . It is worth noting that this commonly used auth method cannot exist on its own without being paired with a tunneling suite.
They also offer a similar level of security, as both protocols can use 256-bit encryption and the highly-secure AES cipher. Right now, the OpenVPN protocol is believed to be the most secure VPN protocol available. Even though it doesn’t offer the fastest possible speeds, it can safeguard your private data in a highly secure way. When it comes to IPSec, this protocol comes with capable encryption but it’s still not fully explored in terms of its security and potential vulnerabilities. IKEv2/IPSec presents a new challenger to OpenVPN, improving on L2TP and other IPSec-based protocols with faster connections, more stability, and built-in support on most newer consumer devices.
Compatibility Native in most desktop, mobile device and tablet operating systems. Native in most desktop, mobile device and tablet operating systems. Supported by most desktop computer operating systems and Android mobile and tablet devices. It is a good choice if OpenVPN isn’t supported by your device. L2TP/IPsec is a good choice if OpenVPN isn’t supported by your device and security is top priority.
Also, L2TP/IPsec is secure enough for most stuff, but the Snowden papers showed it can be cracked by the NSA. At its core, OpenVPN uses a custom model combining Secure Sockets Layer (SSL) and Transport Layer Security (TLS) to provide encryption. These protocols allow OpenVPN to utilize public-key cryptography, which thus allows it to implement a secure connection over HTTP. Generally, you should choose a VPN provider that provides access to OpenVPN connections, but which also offers access to other VPN protocols. OpenVPN is both a VPN protocol and software that uses VPN techniques to secure point-to-point and site-to-site connections.
This hides information such as a type of packet, where its final destination is and so on. Encryption is the technology used to encode and decode the data itself.
Fast support
IPSec and SSL are the two most popular secure network protocol suites used in Virtual Private Networks, or VPNs. IPSec and SSL are both designed to secure data in transit through encryption. The best protocols for peer to peer downloading/torrenting are OpenVPN and SSTP as they are best for anonymity and security. Some may recommend L2TP/IPsec to assist in increasing download speeds, but as L2TP/IPsec has security flaws, I would stay away from it when torrenting. It’s also important that you use a service with the VPN kill switch feature to make sure that if your connection does drop, your torrenting activity isn’t exposed.