Hash function
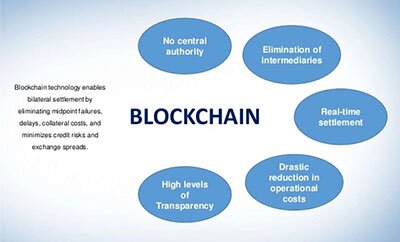
The database is not managed by any particular body; instead, everyone in the network gets a copy of the whole database. Old blocks are preserved forever and new blocks are added to the ledger irreversibly, making it impossible to manipulate by faking documents, transactions and other information.
What is Blockchain simple explanation?
A Blockchain is a type of diary or spreadsheet containing information about transactions. Each transaction generates a hash. If a transaction is approved by a majority of the nodes then it is written into a block. Each block refers to the previous block and together make the Blockchain.
Each individual has these two keys, which they use to produce a secure digital identity reference. This secured identity is the most important aspect of Blockchain technology.
The “proof of work” system that bitcoin uses to validate transactions, for example, consumes vast amounts of computational power. In the real world, the power from the millions of computers on the bitcoin network is close to what Denmark consumes annually.
Also, the Bitcoin blockchain is very resilient and would quickly adapt as a response to an attack. Even though personal information on the blockchain is kept private, the technology itself is almost always open source. That means that users on the blockchain network can modify the code as they see fit, so long as they have a majority of the network’s computational power backing them. Keeping data on the blockchain open source also makes tampering with data that much more difficult. With millions of computers on the blockchain network at any given time, for example, it is unlikely that anyone could make a change without being noticed.
However, its decentralized nature also brings some disadvantages. For instance, when compared to traditional centralized databases, blockchains present limited efficiency and require increased storage capacity. Although blockchain can save users money on transaction fees, the technology is far from free.
But it turns out that blockchain is actually a pretty reliable way of storing data about other types of transactions, as well. In fact, blockchain technology can be used to store data about property exchanges, stops in a supply chain, and even votes for a candidate. Even if a user receives a payment in bitcoins to their public key, they will not be able to withdraw them with the private counterpart. A user’s public key is a shortened version of their private key, created through a complicated mathematical algorithm.
There is the additional complication that it is possible to register a Bitcoin address that has no links to the holder’s real-world identity. However, this is a potential criticism of the cryptocurrency system and not related to the security of the Blockchain technology itself. Blockchain technology is, in fact, a group of different technologies that can be used together in different ways to create different end results or applications. While the details will vary between Blockchain protocols, the core of the technology is that it is a decentralized digital ledger of transactions. These transactions are verified in whatever way is deemed appropriate for the particular Blockchain application.
The Proof of Work consensus algorithm that protects the Bitcoin blockchain has proven to be very efficient over the years. However, there are a few potential attacks that can be performed against blockchain networks and 51% attacks are among the most discussed.
Distributed database
In digital currency cases, this verification is used to approve transaction blocks before they are added to the chain. This mechanism could just as easily be applied to other types of verification procedures, including identity verification and many other applications as well.
In the case of Bitcoin, the sender must present a private key, signifying ownership, and a public key, which represents the ‘address’ of the digital wallet the Bitcoin is held in. As its name implies, a blockchain is a chain of blocks, which are bundles of data that record all completed transactions during a given period. For bitcoin, a new block is generated approximately every 10 minutes.
- Blockchain transaction ledgers are also decentralized, which means copies exist on numerous ‘nodes’.
- In the case of public Blockchains such as cryptocurrencies, the number of nodes can reach millions.
- Nodes are computers participating in a particular Blockchain application.
Many blockchain networks operate as public databases, meaning that anyone with an internet connection can view a list of the network’s transaction history. Although users can access details about transactions, they cannot access identifying information about the users making those transactions. It is a common misperception that blockchain networks like bitcoin are anonymous, when in fact they are only confidential. Blocks on the blockchain store data about monetary transactions—we’ve got that out of the way.
Where can Blockchain be used?
All of that energy costs money and according to a recent study from research company Elite Fixtures, the cost of mining a single bitcoin varies drastically by location, from just $531 to a staggering $26,170. I bet most of the enterprise systems do not want to be public, transparent, or distributed. Also, a system built on blockchain does not only take a longer time to process transactions, but also requires many more times the resources, such as processing, electricity, and data transfer.
Through the use of public and private keys blockchains can be encrypted. The private key is a password that gives access to your transactions. The problem with public/private keys is that if you lose the private decryption key, you may not be able to retrieve certain information. One way to deal with that is to safeguard your private key by printing it out (a “paper wallet”).
Mining involves generating the hash of a block transaction, which is tough to forge, thereby ensuring the safety of the entire Blockchain without needing a central system. Cryptography keys consist of two keys – Private key and Public key. These keys help in performing successful transactions between two parties.
In most traditional payment systems, transactions are not only dependent on the two parties involved, but also on an intermediary – such as a bank, credit card company, or payment provider. When using blockchain technology, this is no longer necessary because the distributed network of nodes verify the transactions through a process known as mining. For this reason, Blockchain is often referred to as a ‘trustless’ system. Based on average utility costs in the United States, that figure is closer to $4,758.

Digital signature
In the world of cryptocurrency, this identity is referred to as ‘digital signature’ and is used for authorizing and controlling transactions. Cryptocurrencies of all types make use of distributed ledger technology known as blockchain. Blockchains act as decentralized systems for recording and documenting transactions that take place involving a particular digital currency. Put simply, blockchain is a transaction ledger that maintains identical copies across each member computer within a network. The fact that the ledger is distributed across each part of the network helps to facilitate the security of the blockchain.
Blockchain transaction ledgers are also decentralized, which means copies exist on numerous ‘nodes’. Nodes are computers participating in a particular Blockchain application. In the case of public Blockchains such as cryptocurrencies, the number of nodes can reach millions. For a change to be made to a Blockchain, at least 51% of the participating nodes must verify it. For new transactions, this means that 51% of the network must be satisfied the verification criteria have been met ie.
However, due to the complexity of this equation, it is almost impossible to reverse the process and generate a private key from a public key. For this reason, blockchain technology is considered confidential. In fact, neither Bitcoin nor Ethereum have ever been hacked. Both Blockchains have remained absolutely secure and are, due to the qualities explained, almost certain to remain so. What many people confuse with Bitcoin or Ethereum being hacked is actually cryptocurrency exchanges or online wallets being hacked.
Most blockchains are designed as a decentralized database that functions as a distributed digital ledger. These blockchain ledgers record and store data in blocks, which are organized in a chronological sequence and are linked through cryptographic proofs. The creation of blockchain technology brought up many advantages in a variety of industries, providing increased security in trustless environments.
Blockchain technology uses hash encryption to secure the data, relying mainly on the SHA256 algorithm to secure the information. The address of the sender (public key), the receiver’s address, the transaction, and his/her private key details are transmitted via the SHA256 algorithm. The encrypted information, called hash encryption, is transmitted across the world and added to the Blockchain after verification. The SHA256 algorithm makes it almost impossible to hack the hash encryption, which in turn simplifies the sender and receiver’s authentication. Blockchain offers a tremendous level of security, thanks to independent verification processes that take place throughout member computers on a blockchain network.
Despite the costs of mining bitcoin, users continue to drive up their electricity bills in order to validate transactions on the blockchain. That’s because when miners add a block to the bitcoin blockchain, they are rewarded with enough bitcoin to make their time and energy worthwhile. When it comes to blockchains that do not use cryptocurrency, however, miners will need to be paid or otherwise incentivized to validate transactions.
Blockchain is a distributed database existing on multiple computers at the same time. It is constantly growing as new sets of recordings, or ‘blocks’, are added to it. Each block contains a timestamp and a link to the previous block, so they actually form a chain.
Once a block is finalized or mined, it cannot be altered since a fraudulent version of the public ledger would quickly be spotted and rejected by the network’s users. Despite being theoretically possible, there was never a successful 51% attack on the Bitcoin blockchain. As the network grows larger the security increases and it is quite unlikely that miners will invest large amounts of money and resources to attack Bitcoin as they are better rewarded for acting honestly.